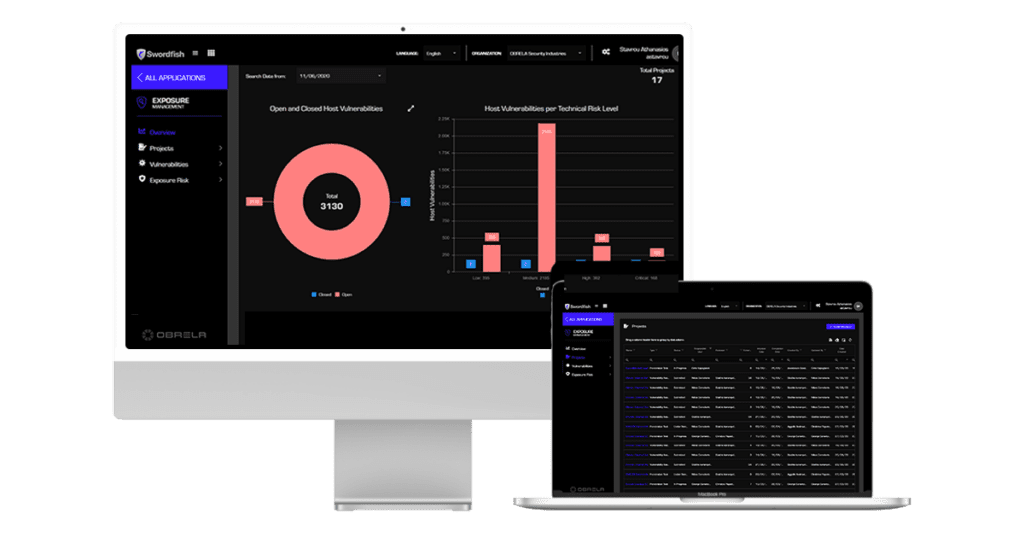
Exposure Management Console (EMC)
SWORDFISH EMC provides a flexible and personalized interface, enabling users to monitor and visualize report statistics, criticality, and resolution status based on their defined parameters. It supports distinct user roles, workflow transitions, and role relationships.





EMC DATASHEET
Access the datasheet and learn more