WHY SWORDFISH
SWORDFISH® Risk Management capabilities combine both Threat Detection and Response (MDR) and the Managed Risk and Controls (MRC) services to resolve technology fragmentation and process disconnects, while incorporating the business perspective into the decision-making process.
SWORDFISH integrates people, processes, and technology, providing 3D (three-dimensional) security as the foundation of next-generation cybersecurity by controlling and monitoring not only technology-related aspects but also procedures that involve the human factor, enhancing situational awareness for clients and bolstering their operational resilience.
The process automation powered by SWORDFISH generates security-related data and records that were previously inaccessible. This data can now be utilized to feed risk analytics engines, resulting in advanced intelligence and a comprehensive, three-dimensional view of enhanced security.
SWORDFISH harnesses the power of its Graph Database to offer robust risk analytics and visualization tools that can turn raw data into actionable insights. By correlating seemingly unrelated data feeds under common or individualistic business-wise approaches, SWORDFISH helps organizations gain valuable insights into their operations.
With SWORDFISH, security, business, and behavioral analytics and risk models can be leveraged to measure the efficiency of controls, assess risks, and identify emerging and advanced cyber threat patterns. The solution also enables users to create different types of dynamic or multi-layered animated graphs, consuming regular or big datasets, without compromising overall system performance. This empowers organizations to make data-driven decisions and stay ahead of potential risks or threats.
SWORDFISH employs an underlying dynamic ontology schema that can be useful for easily harmonizing data and creating linked and contextualized content that depicts interrelationships between data entities, enabling deeper meaning, insight, and action. Ontology creation allows for significant time savings on harmonizing, linking, contextualizing, and preparing data and making it easy for users to conduct self-serve discovery, analytics, and data utilizations.
SWORDFISH provides near real-time reporting and measurement of compliance, with centralized repositories that cover deviations from over 20 regulatory and widely accepted frameworks. You can track compliance status, summarize assessment results, and plan remediation through tailored workflows and centralized case management, all from one place. Historical benchmarking data is also available to help you track your compliance progress over time.
 ">
">How Risk
Becomes Reward
The Swordfish real-time, risk management platform centralizes data across your enterprise to bring business perspective to every cybersecurity decision.

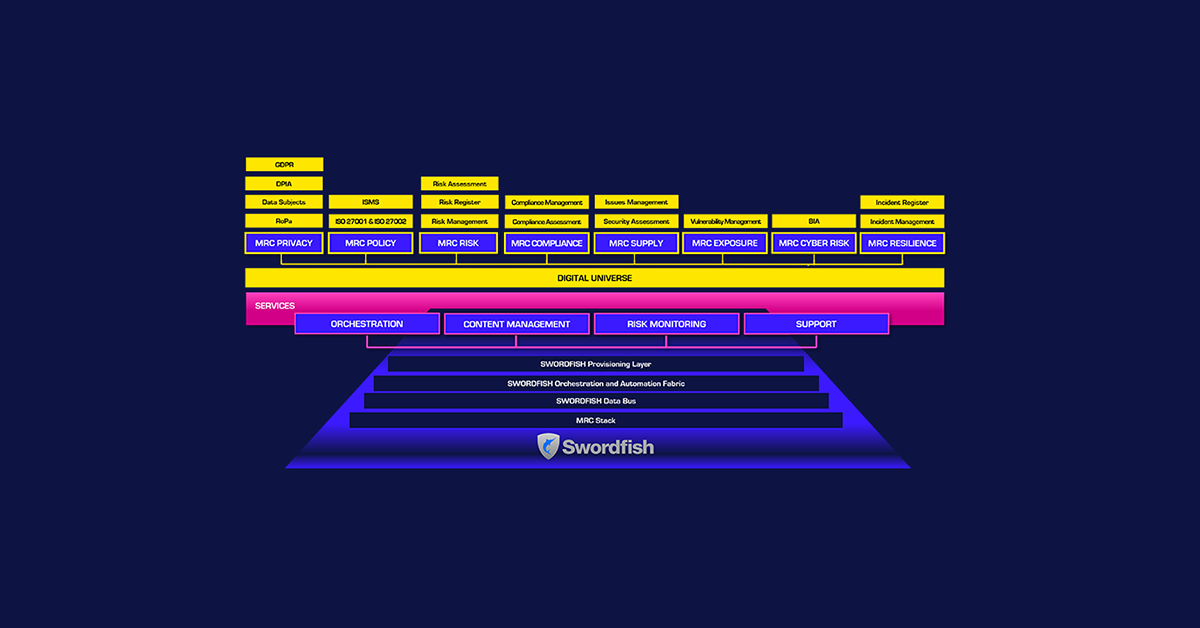
SWORDFISH TECHNOLOGY
Swordfish technology enables real-time fusion of threat-related data with workflow data from governance, risk, compliance and operations security activities, allowing for identification and assessment of actual risks, not just threats, in a customer-focused and risk-based context. This integrated approach ensures that potential risks are analyzed and prioritized according to their potential impact on the organization, and allows for more effective and efficient allocation of resources to mitigate risks. By utilizing Swordfish technology, organizations can gain a more comprehensive understanding of their security posture and prioritize their resources to mitigate actual risks, rather than simply reacting to threats after they occur.

ADDRESS SECURITY REQUIREMENTS
SWORDFISH for MRC further, serves as a central layer for MRC provisioning, offering with the necessary content, applications, and tools for designing and coordinating operations and service delivery to address various security requirements, such as governance, compliance and risk management, privacy management, vulnerability management and supply chain security. It also provides a uniform customer interface to service outcomes enhanced with risk analytics and visualizations.


BOOK YOU DEMO
Complete the form and Discover how Obrela’s Swordfish Platform can empower your organization to achieve a resilient cybersecurity posture